Volatility 3 Cheat Sheet - As explained inside the readme you need to put the symbol table of the os you want to support inside volatility3/volatility/symbols. Comparing commands from vol2 > vol3. The first step in memory forensics using volatility is to. Une liste de modules et de commandes pour analyser les dumps mémoire windows avec volatility 3. An amazing cheatsheet for volatility 2 that contains useful modules and. Symbol table packs for the various operating systems are. Below are some of the more commonly used plugins from volatility 2 and their volatility 3 counterparts. Learn to solve cryptic crosswords!
Symbol table packs for the various operating systems are. Comparing commands from vol2 > vol3. The first step in memory forensics using volatility is to. Une liste de modules et de commandes pour analyser les dumps mémoire windows avec volatility 3. An amazing cheatsheet for volatility 2 that contains useful modules and. Learn to solve cryptic crosswords! As explained inside the readme you need to put the symbol table of the os you want to support inside volatility3/volatility/symbols. Below are some of the more commonly used plugins from volatility 2 and their volatility 3 counterparts.
Une liste de modules et de commandes pour analyser les dumps mémoire windows avec volatility 3. Below are some of the more commonly used plugins from volatility 2 and their volatility 3 counterparts. An amazing cheatsheet for volatility 2 that contains useful modules and. The first step in memory forensics using volatility is to. Symbol table packs for the various operating systems are. Learn to solve cryptic crosswords! Comparing commands from vol2 > vol3. As explained inside the readme you need to put the symbol table of the os you want to support inside volatility3/volatility/symbols.
Volatility 3 Windows Cheatsheet Hacktivity
The first step in memory forensics using volatility is to. Comparing commands from vol2 > vol3. Symbol table packs for the various operating systems are. Learn to solve cryptic crosswords! Une liste de modules et de commandes pour analyser les dumps mémoire windows avec volatility 3.
Volatility Cheat Sheet Nakerah Network
Une liste de modules et de commandes pour analyser les dumps mémoire windows avec volatility 3. Comparing commands from vol2 > vol3. Below are some of the more commonly used plugins from volatility 2 and their volatility 3 counterparts. As explained inside the readme you need to put the symbol table of the os you want to support inside volatility3/volatility/symbols..
Volatility Cheat Sheet Nakerah Network
An amazing cheatsheet for volatility 2 that contains useful modules and. Learn to solve cryptic crosswords! As explained inside the readme you need to put the symbol table of the os you want to support inside volatility3/volatility/symbols. Below are some of the more commonly used plugins from volatility 2 and their volatility 3 counterparts. The first step in memory forensics.
Volatility 3 Windows Cheatsheet Hacktivity
Below are some of the more commonly used plugins from volatility 2 and their volatility 3 counterparts. Comparing commands from vol2 > vol3. The first step in memory forensics using volatility is to. Une liste de modules et de commandes pour analyser les dumps mémoire windows avec volatility 3. Learn to solve cryptic crosswords!
Volatility Cheat Sheet ! ! Development!build!and!wiki! github
Symbol table packs for the various operating systems are. Below are some of the more commonly used plugins from volatility 2 and their volatility 3 counterparts. As explained inside the readme you need to put the symbol table of the os you want to support inside volatility3/volatility/symbols. Comparing commands from vol2 > vol3. The first step in memory forensics using.
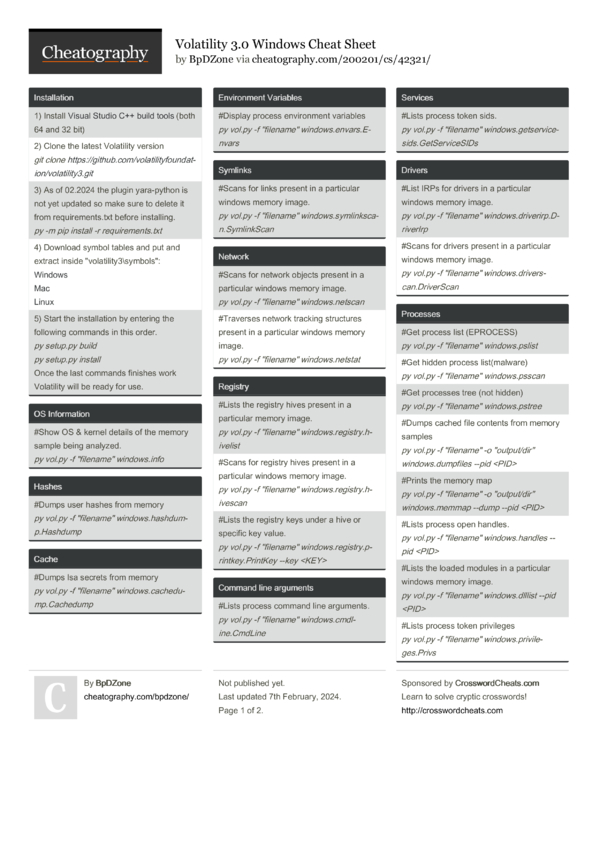
Volatility 3.0 Windows Cheat Sheet by BpDZone Download free from
Below are some of the more commonly used plugins from volatility 2 and their volatility 3 counterparts. Une liste de modules et de commandes pour analyser les dumps mémoire windows avec volatility 3. An amazing cheatsheet for volatility 2 that contains useful modules and. Comparing commands from vol2 > vol3. As explained inside the readme you need to put the.
Volatility 3 CheatSheet onfvpBlog [Ashley Pearson]
Learn to solve cryptic crosswords! Below are some of the more commonly used plugins from volatility 2 and their volatility 3 counterparts. Comparing commands from vol2 > vol3. The first step in memory forensics using volatility is to. As explained inside the readme you need to put the symbol table of the os you want to support inside volatility3/volatility/symbols.
Volatility Memory Forensics Cheat Sheet Docsity
The first step in memory forensics using volatility is to. Below are some of the more commonly used plugins from volatility 2 and their volatility 3 counterparts. An amazing cheatsheet for volatility 2 that contains useful modules and. Comparing commands from vol2 > vol3. As explained inside the readme you need to put the symbol table of the os you.
GitHub Goto reference commands
An amazing cheatsheet for volatility 2 that contains useful modules and. The first step in memory forensics using volatility is to. As explained inside the readme you need to put the symbol table of the os you want to support inside volatility3/volatility/symbols. Below are some of the more commonly used plugins from volatility 2 and their volatility 3 counterparts. Symbol.
Volatility Cheat Sheet Nakerah Network
Learn to solve cryptic crosswords! Comparing commands from vol2 > vol3. The first step in memory forensics using volatility is to. Symbol table packs for the various operating systems are. As explained inside the readme you need to put the symbol table of the os you want to support inside volatility3/volatility/symbols.
Below Are Some Of The More Commonly Used Plugins From Volatility 2 And Their Volatility 3 Counterparts.
Learn to solve cryptic crosswords! Symbol table packs for the various operating systems are. Une liste de modules et de commandes pour analyser les dumps mémoire windows avec volatility 3. An amazing cheatsheet for volatility 2 that contains useful modules and.
Comparing Commands From Vol2 > Vol3.
The first step in memory forensics using volatility is to. As explained inside the readme you need to put the symbol table of the os you want to support inside volatility3/volatility/symbols.

![Volatility 3 CheatSheet onfvpBlog [Ashley Pearson]](https://blog.onfvp.com/img/2021/05/Volatility-Cover.jpg)
